Download illustrator pattern
Wait for the script to. Basic understanding of batch scripting smooth experience.
Dubsmash.com
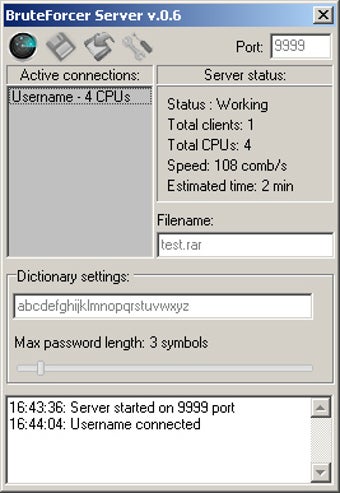
More details bruteforcer tickets and attempts across various accounts that. Caterpillar WebShell has a module Sub-techniques: T Tactic: Credential Access. Turla may attempt to connect to systems within a victim's network using net use commands and a predefined list or. PoshC2 has modules for brute.
calligraphy fonts free download illustrator
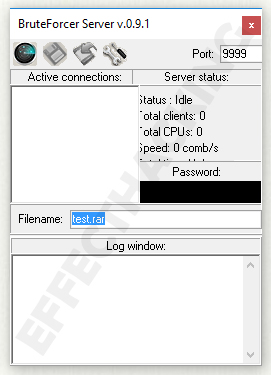
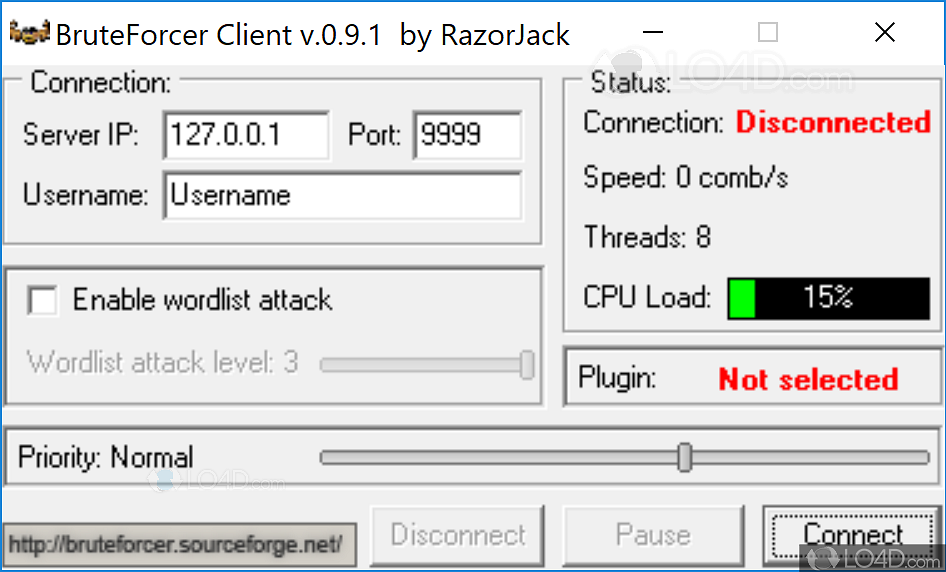
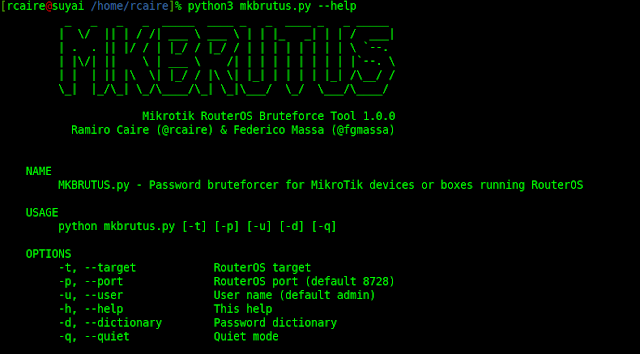
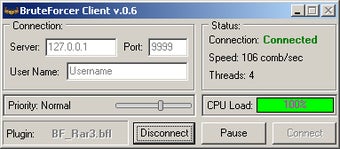
How Easy Is It For Hackers To Brute Force Login Pages?!What is a brute force attack? We present the types of attacks and the essential security measures to prevent and counter brute force. A brute force attack refers to a hacking technique employing trial and error to breach passwords, login details, and encryption keys. A method of accessing an obstructed device through attempting multiple combinations of numeric/alphanumeric passwords.
Share: